bt.exe reflection
Last week I addressed the question "Are privacy limits something that should be considered when breaking boundaries with meta narrative?" with a small mind map that, honestly, kind of moved beyond the boundaries of this question. It's very hard to stick to the one point when the questions all around the boundaries are just as interesting, plus I'm a very curious person by nature. However, this question is a bit of objective one.
In my day job, lecturing in web and games at SAE, I see a lot of different people come through that are not exactly sharing the same demographic as me. One thing in particular I noted was that there is a massive divide between what a lot of them considered private data and what the older lecturers considered private data. This schism of what would be considered a privacy limit is something that must be kept in mind in answering this question.
I myself have a little bit of a twisted idea of privacy, knowing full well what kind of data I put on the internet is private and which is public. I know for a fact that my location at any given point is being recorded and could be retrieved by someone with enough determination. I know that almost everything that I post on any social media could come back to haunt me (thus the multiple social medias). I know that any SMS that arrives on my phone has absolutely no encryption and could be read at any time.
This informs how I view privacy myself, and to an extent means that something as simple as facebook stalking (an act which some would call quite creepy) is no different from just looking up information in a library. This data is entirely public to my knowledge, even if it is not considered so in the public eye. So, I would not say my understanding of privacy is the cultural norm, and thus any boundary I build myself is flawed. Therefore, any way that I try to answer this question must keep it in mind.
As I pondered exactly how I should answer this question in a creative way, I thought instead of defining what might be considered the accepted privacy boundary perhaps I could test to see if I could go overboard. I could then sit there are record some data about how people interacted with both the creative piece and any sharing that was done on it. Based off this data I could get an idea of how people reacted to it.
So I began to build, my idea was quite simple. A couple of years ago I found a site by Robin Linus that exposed a lot of data from the browser that could easily be collected without any issues. My thought was that if I could weave that information into an online narrative in order to scare the player it could really push that boundary of private data as far as it could. My choice to do a more horror / creepy narrative came from my mindmap, as generally I had found in narrative the two options I had was camp comedy or horror. While this privacy meta narrative has been used elsewhere, these are the two most memorable styles that it could take.
So… I have a direction and some data I could use, how can I use it. What exactly is the scariest thing someone could come across on the internet…
It's viruses. The idea that at any point clicking a malicious link on the internet could entirely reveal their location, data or even destroy their computer. Finding an unexpected and unwelcome passenger on your internet connection is literally something that everyone has experienced at some point to various effects.
Sometimes it's as simple as monitoring your data and providing it to companies so they can target you better, slowing down your computer or changing your default search engine.
However, on the opposite end of the spectrum with have purely malicious intent. This can be seen in programs such as Malware, that locks your data behind a paywall.
It doesn't help that popular news sites are often talking about big scares in the online world, horrible applications that are spreading through the digital world. Programs like WannaCry that are incredibly dangerous in who they target and how powerful they are.
Sidenote here: If you want to read something quite interesting, look at what is happening to Marcus Hutchins, the developer who stopped WannaCry in its tracks. He ended up getting arrested by the FBI earlier this month.
So! My idea is to build a fake virus, something that looks absolutely terrifying and pretends to know your computer inside and out. I can pull this meta data through the browser to enhance this narrative and make it as believable as possible. To offset the actual realism of this I would create a cute little pixel creature as the titular virus character. And thus, bt.exe was born.

Now, I will be the first to admit that I went a little… off the tracks while creating this narrative. As I was writing it I had a handful of data I could collect next to me, and my intent was to weave it into the narrative as seamlessly as possible. The project by Robin Linus was already listing all this data (and more) but it just didn't feel as creepy since it was almost a table of data that was being put before the user. The virus needed to have a reason to be telling you it needed this information.
As I progressed through the original draft of the piece I realised that the player needed to be able to communicate with the virus as the conversation went forward, so I created a small 'reply' feature where the user could hit the response they wanted to give. Originally all of these replies led to the same statements from BT, but I felt added a little bit of something from the player. I generally wrote the script by building a set of statements that would reveal the data, followed by the most obvious response a player would like to give. And this… changed the game in a way.
The most likely response 90% of the time I would assume was outrage, confusion or demanding to know why this data was public (this ended up following the responses I got from players of the game, so I feel that this assumption is valid). And since this is the response from the player, BT had to address what they said. Without meaning to, I had pushed this game in another direction simultaneously, a conversation about privacy on the internet.
On one hand I was reluctant to leave it as it stood, it was not meant to be a conversation about that particular narrative. However, this didn't bother me overly as this is information I think should be shared regardless. In order to continue this conversation I added a window at the game, explaining what I was trying to communicate in an attempt to both help with the understanding and to drive communication forward.
But what is a project without testing?
Quietly I forwarded the project to 5 people I thought would be interested and 1 I was sure would give me feedback that would help me make this a better experience. The feedback I got was as follows:
Ooooooo this gave me the heebeegeebees
I don't like this
IS NO LONGER ACCEPTING LINKS FROM THIS USER
Three things, you need to change the font, make it obvious when BT has stopped talking and I hate it that almost all the choices in replies are just reworded versions of the same thing
So I did a couple of quick changes. Originally in my head I thought that just having two possible answers every time would be consistent, but instead I made it change depending on the point of the story. I also considered making this into part of the narrative itself, changing it so that the last question asked "You will just have to live in a world without privacy… do you agree?" which originally had a yes and a no answer would actually remove the no answer if you tried to chose it (making a comment that all your answers so far were kind of useless anyway.
So I had the creative work, that was half the job done, I needed to share it. I posted two posts on twitter:
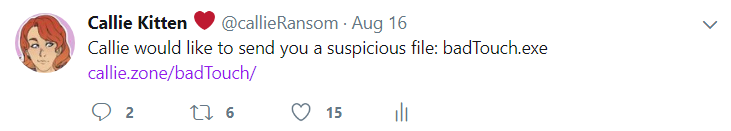
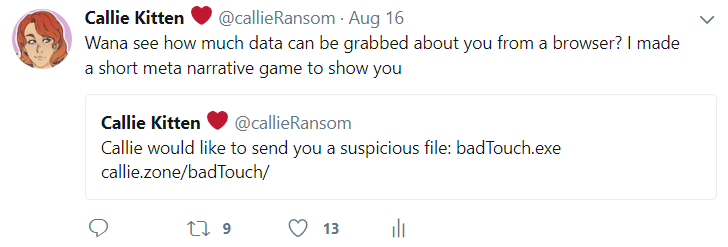
The first post is a bit catchy, a bit clickbaity and it works well in the fiction of the narrative. The second is more of a thinking person's post. It explains the purpose and makes it less of a scary, clickbaity situation. I was hoping that the combination of these two posts would help a lot. So… how did they do?
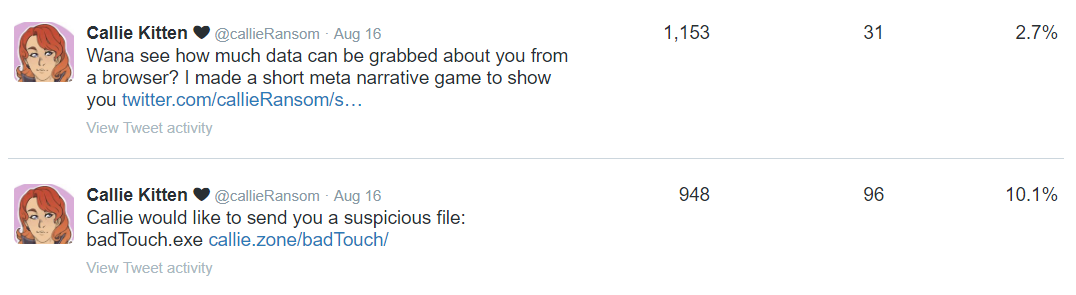
So we have a little bit of a conundrum here. It seems that the malicious in narrative link was five times more likely to be clicked, but the nicely worded explanation post was more likely to be shared, as it reached a larger audience. This led me to my first thought in regards to answering this question.
People have an almost perverse desire to see how far this virus will go, will it discover things they never thought possible. However, they are not willing to risk sharing such a thing as they either worry about the repercussion of a friend freaking out or they worry about their social image.
This was proven by some of the communications i got back about the project.
I was hoping/dreading to see some of my search history coming up. I feel I got away with being really interrogated in that regard.
It's that duality of being worried about it happening to you, and that need to see if it happens. That same reason why people slow down at car crashes to see what has happened. The same reason, quite frankly, why some people really enjoy horror movies. Looking at the report on how long people spent at this page we can definitely see that on average people stayed till the end. This game takes a slow reader 2:50 to complete (not including reading the ending card)
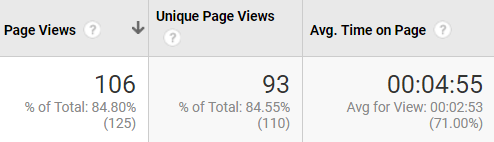
As you can see, the average time taken on the page exceeds the time it takes a slow reader to complete the experience. This means that not only on average were all users getting through the narrative, it is also more than likely they were also reading the card at the end. Regardless of any messages about how creepy this game is, people did not stop playing it at all.
That is not to say that all of the responses I got were necessarily good. I did get a bit of flack for my naming convention. badTouch.exe is… slightly trivialising a pretty serious situation, and it's something I purely used for shock value. Two people on social media directed these comments at me in particular, but I had a conversation with them and I do now regret my choice in naming convention.
I also found that my choice in creation here actually limited the amount of sharing that happened. The fact that this is pretending to be a malicious file, combined with the naming convention did actual limit how much people were willing to share it. While I couldn't have really changed the message and delivery without changing the whole process, once again the naming convention could have been more thoughtful. I guess to an extent I didn't expect people to share this around. I hoped they would, but I have never really made something that got all that popular. This is something that I need to be careful of in the future.
Technical details
Some people asked how I created this, and I think I will just simply discuss this here quickly. A lot of code was used from Robin Linus's page. In particular all the device detection and social media detection code was something I had not experimented with before. I had played around with rotation detection and I did tweak his code a lot to make it play a little bit nicer, however I ended up removing this code from the finish production (more on that in the next section).
Outside of that, the actual code that is used to control the interaction with BT and the player is entirely handcoded using Jquery. Yes, I'm mad. Yes, I could have done it a lot faster with a framework. But, I couldn't have tweaked it as freely.
What was removed / what doesn't work
So there are a couple of things I removed from the game, a couple that never work and a couple that almost never work.
There originally was a script so that when the player put down their phone on a table it screamed "Don't ignore me". While this was a great little bit of meta narrative it turned out a couple of very steady handed players could get this to trigger no matter how fine I tuned it. This would continuously fire off during narrative and ruin the experience.
There is code in the game that used the ambient light reader built into some devices to tell how brightly lit the player was and with what kind of light. It could use this to tell if you were inside, outside or in a dark place and would make comments accordingly. However, this is barely supported by any combinations of device / browser and so will likely never be seen.
Finally, the code to detect the player's location is… very inaccurate. Depending on the location of the player it can give incredibly bad reports of where the player is, especially outside of major cities. While this can create a wrong impression in maybe 20% of the people playing the game, I left it in as the remaining 80% are hugely affected by this peice of narrative.
Final thoughts
This was awesomely fun to make, and I'm glad to have it lying around my site now. This has also inspired me to focus on build small, quick bits of narrative and gameplay as I could do it in a couple of days and people are more likely to invest a few minutes to try something out. I get to experiment freely and I put out more projects.
I'm considering building a new section of this site simply for listing these small projects, even if it is just to encourage me to keep doing it.
References
Google Analytics. (2017). Google Analytics. Retrieved 25 August 2017, from https://analytics.google.com/analytics/web/
Linus, R. (2017). What every Browser knows about you. Webkay. Retrieved 25 August 2017, from http://webkay.robinlinus.com/
Reporters, T. (2017). WannaCry hero Marcus Hutchins freed from US jail ahead of court appearance on malware charges. The Telegraph. Retrieved 25 August 2017, from http://www.telegraph.co.uk/technology/2017/08/08/wannacry-hero-marcus-hutchins-freed-us-jail-ahead-court-appearance/
Twitter analytics - Callie Ransom. (2017). Analytics.twitter.com. Retrieved 25 August 2017, from https://analytics.twitter.com/user/callieRansom/tweets
What you need to know about the WannaCry Ransomware. (2017). Symantec Security Response. Retrieved 25 August 2017, from https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware